Nearby Threats: Reversing, Analyzing, and Attacking Google’s ‘Nearby Connections’ on Android
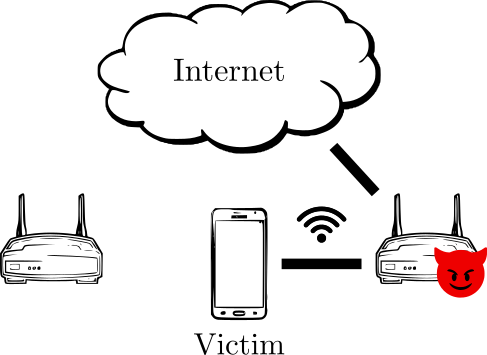 Soft AP Redirection Attack
Soft AP Redirection Attack
Abstract
Google’s Nearby Connections API enables any Android (and Android Things) application to provide proximity-based services to its users, regardless of their network connectivity. The API uses Bluetooth BR/EDR, Bluetooth LE and Wi-Fi to let “nearby” clients (discoverers) and servers (advertisers) connect and exchange different types of payloads. The implementation of the API is proprietary, closed-source and obfuscated. The updates of the API are automatically installed by Google across different versions of Android, without user interaction. Little is known publicly about the security guarantees offered by the API, even though it presents a significant attack surface. In this work we present the first security analysis of the Google’s Nearby Connections API, based on reverse-engineering of its Android implementation. We discover and implement several attacks grouped into two families: connection manipulation (CMA) and range extension attacks (REA). CMA-attacks allow an attacker to insert himself as a man-in-the-middle and manipulate connections (even unrelated to nearby), and to tamper with the victim’s interface and network configuration. REA-attacks allow an attacker to tunnel any nearby connection to remote locations, even between two honest devices. Our attacks are enabled by REArby, a toolkit we developed while reversing the API implementation. REArby includes a dynamic binary instrumenter, a packet dissector, and the implementations of custom Nearby Connections client and server. We plan to open- source REArby after a responsible disclosure period