Reversing and Attacking Google Nearby
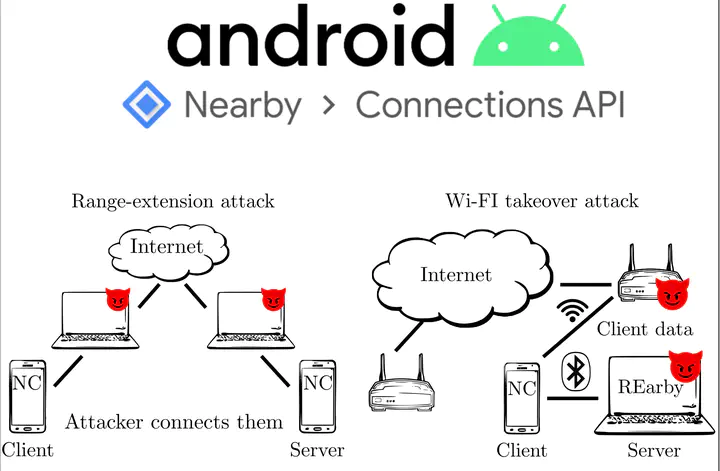
In 2019 in a paper titled Nearby Threats: Reversing, Analyzing, and Attacking Google’s ‘Nearby Connections’ on Android we uncovered issues on Nearby Connections, an proprietary Google API included in all Android devices. The API is used to provide proximity-based services using a combination of Bluetooth and Wi-Fi wireless technologies.
We developed an open-sourced REarby, a toolkit to automate reverse engineering and attacking Nearby Connections.
