Bluetooth KNOB Attacks
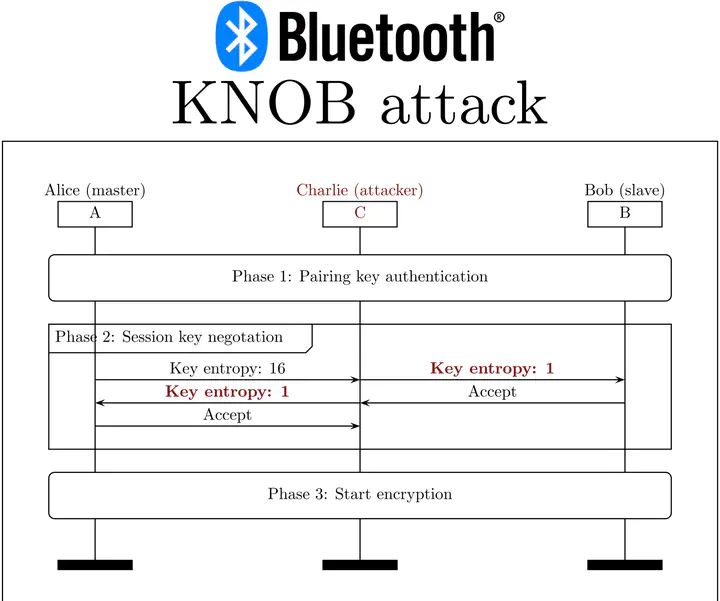
In 2019 we disclosed two families of high impact attacks affecting the entropy negotiation protocols of Bluetooth Classic (BC) and Bluetooth Low Energy (BLE). We named the attacks Key Negotiation of Bluetooth (KNOB) attacks. They are tracked as CVE-2019-9506.
Our first work titled The KNOB is Broken: Exploiting Low Entropy in the Encryption Key Negotiation of Bluetooth BR/EDR explains how to exploit BC’s entropy negotiation to downgrade the entropy of a Bluetooth security key to 1 byte and then brute-force it.
In a follow-up work titled Key Negotiation Downgrade Attacks on Bluetooth and Bluetooth Low Energy we analyzed also BLE and found that it is vulnerable as well to the KNOB attacks. In this case the attacker can downgrade the entropy of BLE security key to 7 bytes and then brute-force it.





