Bluetooth BIAS Attacks
May 18, 2020
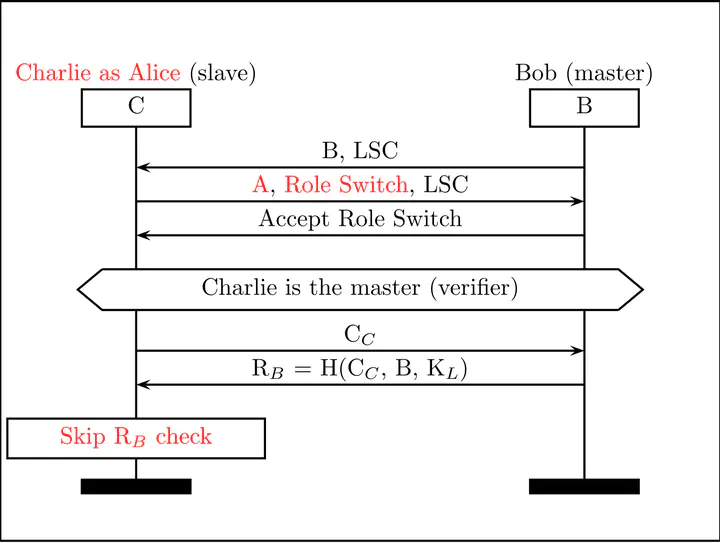
In 2020 we disclosed the Bluetooth Impersonation AttackS (BIAS), a family of high impact attacks affecting Bluetooth’s authentication protocols. The attacks allow impersonating any Bluetooth device during secure session establishment without knowing the long term pairing key. The BIAS attacks are tracked with CVE-2019-9506
IEEE S&P (Oakland) 2020 Paper Teaser
IEEE S&P (Oakland) 2020 Paper Presentation
BIAS + KNOB attack against Bluetooth IACR Attacks in Crypto
From Bluetooth Standard to Standard Compliant 0-days Hardwear.io
Related
Events
In this talk we will explore recent research on real world wireless security protocols. We will cover standard protocols such as Bluetooth pairing and session establishment and proprietary ones such as IoT application layer protocols used to secure traffic between companion mobile applications and electric scooters and fitness trackers.
Jul 22, 2024 00:00
University of Verona (UniVR)
Keynote given at ACSW'24 (EuroS&P Workshop) covering Automotive Bluetooth Security and E-Spoofer.
Jul 8, 2024 00:00
Vienna
This talk covers our recent research on the (in)securities of proprietary and standard wireless security protocols used daily by millions of devices and users. In particular, I will cover the BLUR attacks on Bluetooth, a novel class of threats capable of exploiting Bluetooth Classic from Bluetooth Low Energy and vice versa.
Jun 1, 2023 00:00
Oxford University, CS Dept
Bluetooth is a ubiquitous technology for low power wireless communications. Bluetooth runs on billions of devices including mobile, wearables, home automation, smart speakers, headsets, industrial and medical appliances, and vehicles. As a result, Bluetooth’s attack surface is huge and includes significant threats such as identity thefts, privacy violations, and malicious device control.
Aug 18, 2020 00:00
IACR WAC workshop co-located with CRYPTO 2020




