Bluetooth BLUR Attacks (BLURtooth)
Mar 5, 2022
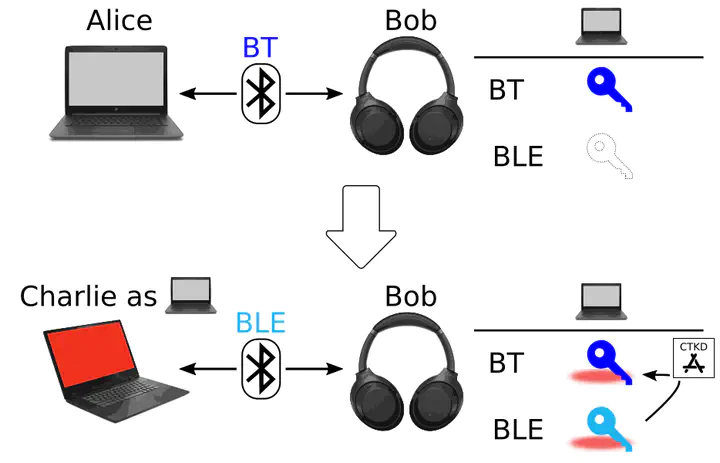
In 2020 we disclosed the BLUR attacks, a family of high impact threats affecting Bluetooth’s cross-transport key derivation (CTKD). The BLUR attacks are the first sample of cross-transport attacks for Bluetooth as they allow to exploit Bluetooth Classic and Bluetooth Low Energy jut by targeting one of the two.
The BLUR attacks are tracked with CVE-2020-15802.
Related
Events
In this talk we will explore recent research on real world wireless security protocols. We will cover standard protocols such as Bluetooth pairing and session establishment and proprietary ones such as IoT application layer protocols used to secure traffic between companion mobile applications and electric scooters and fitness trackers.
Jul 22, 2024 00:00
University of Verona (UniVR)
Keynote given at ACSW'24 (EuroS&P Workshop) covering Automotive Bluetooth Security and E-Spoofer.
Jul 8, 2024 00:00
Vienna
This talk covers our recent research on the (in)securities of proprietary and standard wireless security protocols used daily by millions of devices and users. In particular, I will cover the BLUR attacks on Bluetooth, a novel class of threats capable of exploiting Bluetooth Classic from Bluetooth Low Energy and vice versa.
Jun 1, 2023 00:00
Oxford University, CS Dept


